RFCs are a way for Atlassian to share what we’re working on with our valued developer community.
It’s a document for building shared understanding of a topic. It expresses a technical solution, but can also communicate how it should be built or even document standards. The most important aspect of an RFC is that a written specification facilitates feedback and drives consensus. It is not a tool for approving or committing to ideas, but more so a collaborative practice to shape an idea and to find serious flaws early.
Please respect our community guidelines: keep it welcoming and safe by commenting on the idea not the people (especially the author); keep it tidy by keeping on topic; empower the community by keeping comments constructive. Thanks!
Project Summary
Following our recently published RFC-95 we would like to provide further details on our thinking for dynamic modules on Forge. This RFC contains more details on the implementation of dynamic modules and what developers can expect. With this RFC iteration we are also ensuring that using dynamic module will not impair an app’s Runs on Atlassian eligibility.
- Publish: Jul 3, 2025
- Discuss: Jul 15, 2025
- Resolve: Jul 21, 2025
Problem
Dynamic Modules
Recap RFC-95: dynamic modules and triggers provide numerous benefits such as on-demand feature delivery, reduced app size, and enhanced user experience. By loading only the essential modules at runtime, developers can easily introduce new features or tailor the app to various environments without necessitating app updates.
Users enjoy the flexibility of dynamic modules as it allows them to flexibly customize their Atlassian experience. For instance, a task management app may allow users to activate or deactivate modules for features like calendar integrations or notification preferences based on their workflows. Each installation of an app can use different dynamic module configurations making it a popular feature.
Example Jira trigger module with Jira expression filtering:
A user configured for a work item to be auto assigned to the user based on the work item’s priority. This should work for any work item in project “xxx” (dynamically specified by the user). The app dynamically registers a new trigger listening for ‘avi:jira:created:issue’ and ‘avi:jira:updated:issue’ with expression based filter to receive events only for “xxx” project. As a result the app will populate the assignee field with the user’s name based on selected priority.
Proposed Solution update
Dynamic modules are modules that are added to a specific installation during an app’s runtime. Instead of defining all modules in the manifest file, these modules would be added during app execution. Following this principle we did propose a set of APIs to register, update and delete dynamic modules.
However, as we were looking more into more dynamic app module use cases, we learned that some of them sometimes handle user generated content (UGC). This means we need to ensure data residency compliance so that apps using dynamic modules can still be eligible for Runs on Atlassian - unless the app is using remote storage which will make it ineligible for Runs on Atlassian. We therefore had to revise our previously proposed solution approach.
Manifest Changes
We are proposing a new module type dynamicModule for the app manifest. Note that adding dynamicModule does not trigger a major version update as no elevation of privileges is happening.
Developers will
- define Forge modules that can be created and managed dynamically by the app
- define a handler to be used for fetching dynamic modules by Atlassian systems. This will need to be a lambda function.
Example Manifest
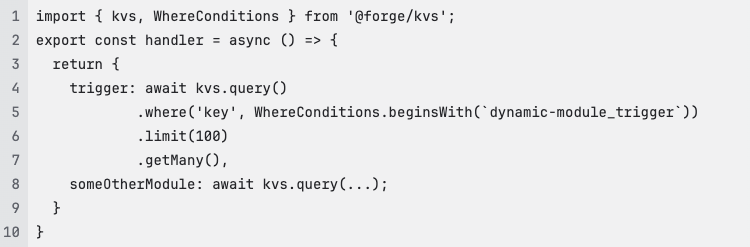
Example implementation of get-dynamic-modules handler using KVS
- Apps will provide a mechanism for customers to create dynamic modules from within the app
- When a new dynamic module is created Atlassian will cache the response for invocations for
dynamicModule. If the invocation is for dynamic module and data is present in cache, then data is returned from the cache. - Atlassian services will discover dynamic modules and subsequently invoke developer defined handlers.
Creating and managing dynamic modules
Persisted key requirements for dynamic modules:
- get a list of available dynamic modules
- register for module types of interest
- update registered modules
- delete registered modules
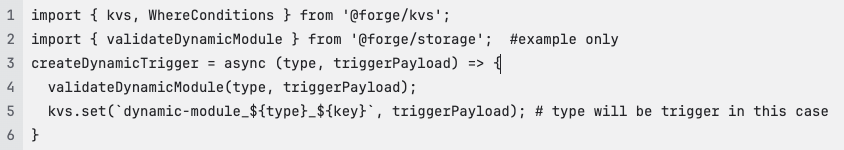
When customers or internal app processes decide they want to create dynamic modules, the app will perform validations and persist dynamic modules within its storage.
An example using KVS can look like
Accessing Dynamic Modules
- When an extension discovery process executes within Atlassian systems, it first locates the
dynamicModulehandler defined in the manifest and then invokes it. - Upon receiving dynamic modules from the handler, Atlassian systems will perform server-side validations.
- This data will then be cached, ensuring that for any subsequent discovery, the invocation process is not re-executed if the data is already present in the cache.
Constraints
- For key collisions between manifest and dynamic modules, manifest defined keys will get preference i.e. dynamic modules will be ignored.
- For collisions between dynamic modules, all such modules will be ignored when processing handler response. For example: if 2 dynamic modules for an installation have a clash, both dynamic modules will be ignored and not available to Atlassian systems.
- We are proposing a limit of 100 dynamic modules per app installation. This has been reviewed based on previous RFC feedback. If the number of dynamic modules returned in the handler response exceeds 100, all dynamic modules for that installation will be ignored.
- Only those modules that are specified in manifest under
useproperty will be discovered. e.g. if app defines triggers as supported dynamic modules but then returns Jira custom fields as well, custom field dynamic modules will be ignored.
We recommend that apps perform client side validations before modifying dynamic modules. This could typically include things like schema validation, payload sizes, complexity of expressions.
Delivery and Improvements
Following RFC feedback we will continue to plan for an iterative delivery starting with trigger modules for Jira. As we progress, we will gradually expand our offerings to additional module types, covering Confluence as well.
We are evaluating the introduction of app notifications about validation failure, however these will not be provided immediately and we are recommending that apps perform client side validations as mentioned above.
Asks
While we would appreciate any reactions you have to this RFC, we’re especially interested in learning more about:
- Are there any major concerns with this new solution approach?
- Is there anything critical you believe we are missing, or which should be reconsidered in the above proposal?